“What does a Cyber Security Practice Model should look like?”, I’ve been asked that question many times over the years, and with the lack of standard in this field, I had and also heard different answers.
Ultimately, I was looking for a simple model where the building blocks of a security practice can be understood even by those who are not experts in the filed. The model I came up with is what I call “The Cyber Security Hierarchy of Needs” and it was inspired by Maslow’s Hierarchy of Needs.
All models are wrong, but some are useful
George Box
The 5 Pillars of Cybersecurity: A Maslow-Inspired Model
Similar to Maslow’s hierarchy of needs, there are 5 pillars (or needs) of cybersecurity that can be visualized as a pyramid, representing a foundational approach to securing information systems. Each pillar builds upon the one below, emphasizing the interconnectedness of various security practices.
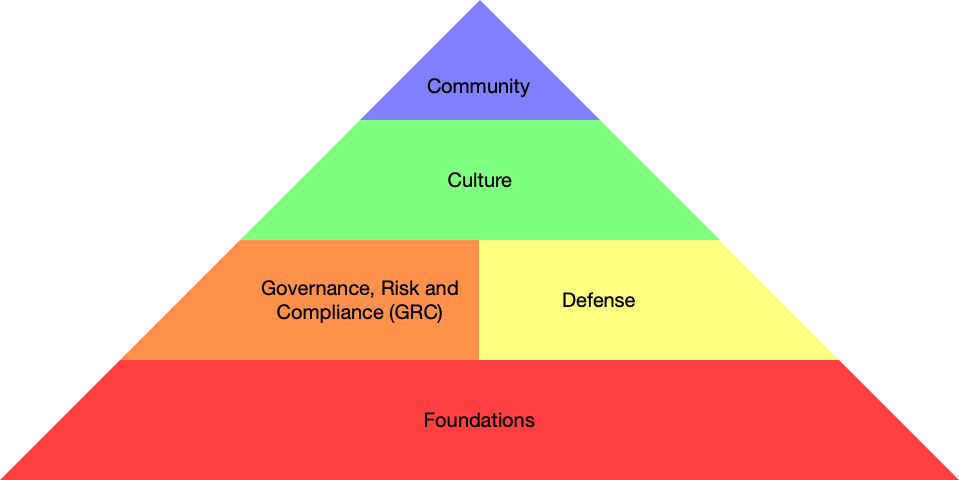
Foundations
The foundations are a set of controls and capabilities that are essential for any security practice for every organization. Another way to think about it is: This is the cost of doing business.
Many people, also call these the basics, but the I don’t like that term. The Basics in the minds of those who are not familiar with the intrinsics of Cyber Security, Basic = Easy, however there is nothing easy in establishing these security foundations and it takes a great deal of effort to implement them consistently and in scale.
Within the foundations, the common controls are things like: Inventory Management, Access Control, Data Protection, Network Security, Vulnerability Management, Secure Configuration, logging and monitoring, etc. A good place to start is to leverage common frameworks like CIS TOP 18 Critical Security Controls, NIST Cyber Security Framework (CSF), etc.
Governance, Risk and Compliance (GRC)
When it comes to GRC, many security practitioners focus only on the C (Compliance) but the the G (Governance) and R (Risk) are equally important. Governance is a decision-making framework that sets the direction and oversees the implementation of cybersecurity strategies and practices. Risk is the process of identifying, evaluating, and prioritizing potential cybersecurity risks and it helps the organization to make calculated choices in utilizing resources in ways that address potential consequences of threats to the business. Lastly, Compliance is the process of adhering to relevant laws, regulations, and industry standards that are designed to protect information and systems from cyber threats. These regulations may be established by government agencies, industry bodies, or internal organizational policies.
I like to think about GRC as the practice that supports the business need to take risks in order to operate effectively, within the boundaries that were set by its own policies, various regulators and governing bodies.
Defense
Defense refers to the strategies, technologies, and practices employed to protect information systems, networks, and data from unauthorized access, use, disclosure, disruption, modification, or destruction. It encompasses a multi-layered approach that involves prevention, detection, mitigation, and response to cyber threats and attacks. It links theory, history, experimentation, and practice to foster initiative and creative thinking in proactive reduction of risk.
In some ways, GRC and Defense are 2 sides of the same coin. If the GRC practice enables the business to assume risk, the Defense practice proactively reduces unnecessary risk.
Culture
An effective security practice requires to enlist everyone to the “Neighborhood Watch”. Educating and empowering users with the right knowledge and capabilities to practice security in their own domain.
Driving security into the culture is not only about education and tools, it is also about given people the right incentives to be part of the security mission.
Community
It takes a village! An effective cybersecurity practice requires forming relationships with the cybersecurity community, alliances and continuous collaboration with industry peers, law enforcement agencies and other partners.
Key points about the model
Needs are hierarchical: Organizations must generally satisfy lower-level pillars before they can move on to higher-level pillars.
Not a rigid order: The model is not meant to be strictly linear, and organizations may move up and down the hierarchy depending on their circumstances.
Needs are continuous: Needs are not completely fulfilled but rather exist on a continuum, and organizations strive to maintain a certain level of practice maturity.
Cultural variations: The importance and order of needs may vary across organizations.
Interconnectedness: Each pillar supports and reinforces the others, creating a comprehensive security posture.
Continuous improvement: The model is not static, and organizations should strive to strengthen each pillar over time.
Tailored approach: The specific implementation of each pillar may vary depending on the organization’s size, industry, and risk profile.
Conclusion
The Cyber Security Hierarchy of Needs model provides a useful and easy to understand framework for organizations of all sizes to assess their cybersecurity posture and identify areas for implementation and improvement. By focusing on building a strong foundation and addressing each pillar comprehensively, organizations can significantly enhance their ability to protect themselves from cyber threats, meet regulatory and client requirements, and meet business goals in a secure and compliant manner.
I hope this blog has given you some food for thought as you practice your security craft, and as always, I would love to hear your thoughts.
